REQUEST CALL
We show you Atribus with a custom DEMO.
- We show you all the functionalities
- Discover the custom reports
- Custom alerts
Discover how your consumers behave in the digital ecosystem.












OUR CUSTOMERS
Big brands that already trust Atribus






FROM DATA TO INSIGHTS
Discover the solutions that Atribus offers you based on the main needs of digital marketing departments.
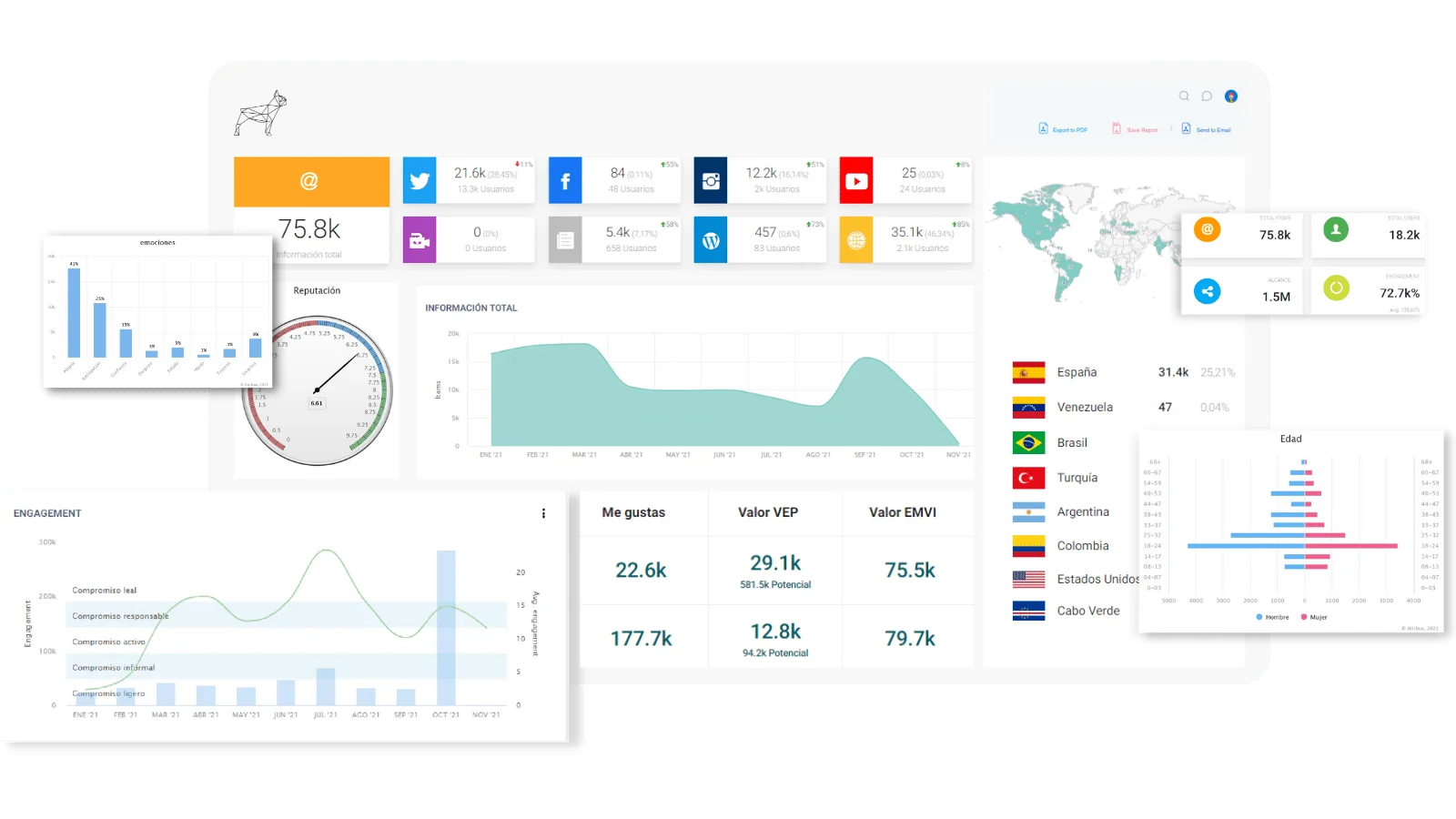
Atribus collects posts from Twitter, Facebook, Instagram, Youtube or LinkedIn among other social media websites. Also, we extract data from Mass Media (online, press, radio, television) including forums, blogs and other websites.
Discover the most influential users in your industry with Atribus. Find the best times to post on social media.
Analyze the behavior of your audience and build a community around your brand.
Create dashboards of your competitors and analyze their strategy.
Always stay one step ahead creating content on upcoming trends.
Customize your reports according to your needs and objectives.
Design, save your templates and optimize your time when creating reports.
Social Competitive Intelligence Software
You are what they say about you online, so understanding your audience is an optimal way to analyze the ROI of your campaigns and focus them toward success.
ANTICIPATE AND KNOW THE MARKET
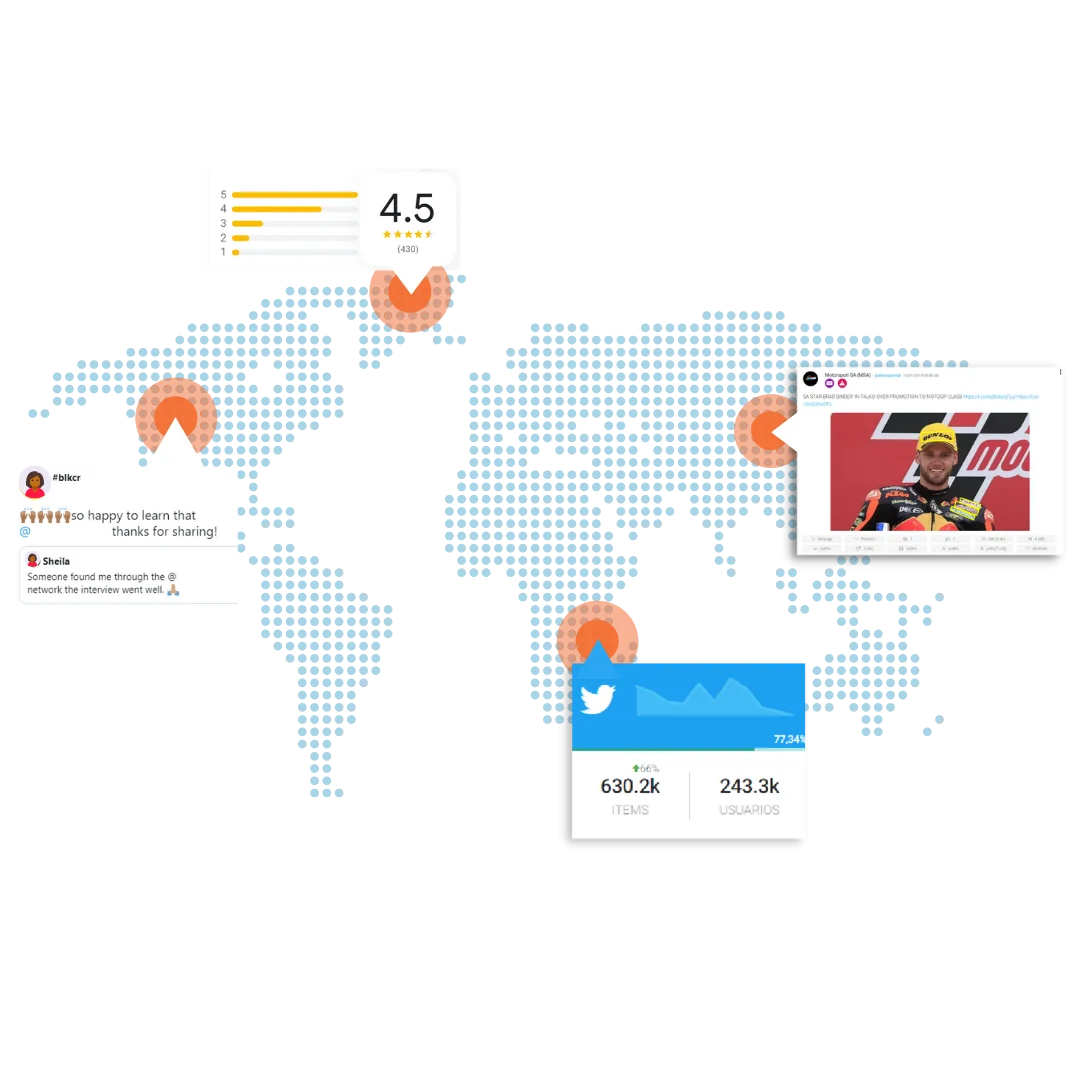
Every day, customers around the world talk about your products, brands or competitors. Be the first to discover new trends and make smarter decisions!
Discover all the Atribus functionalities designed to analyze consumer behavior and focus your campaigns.
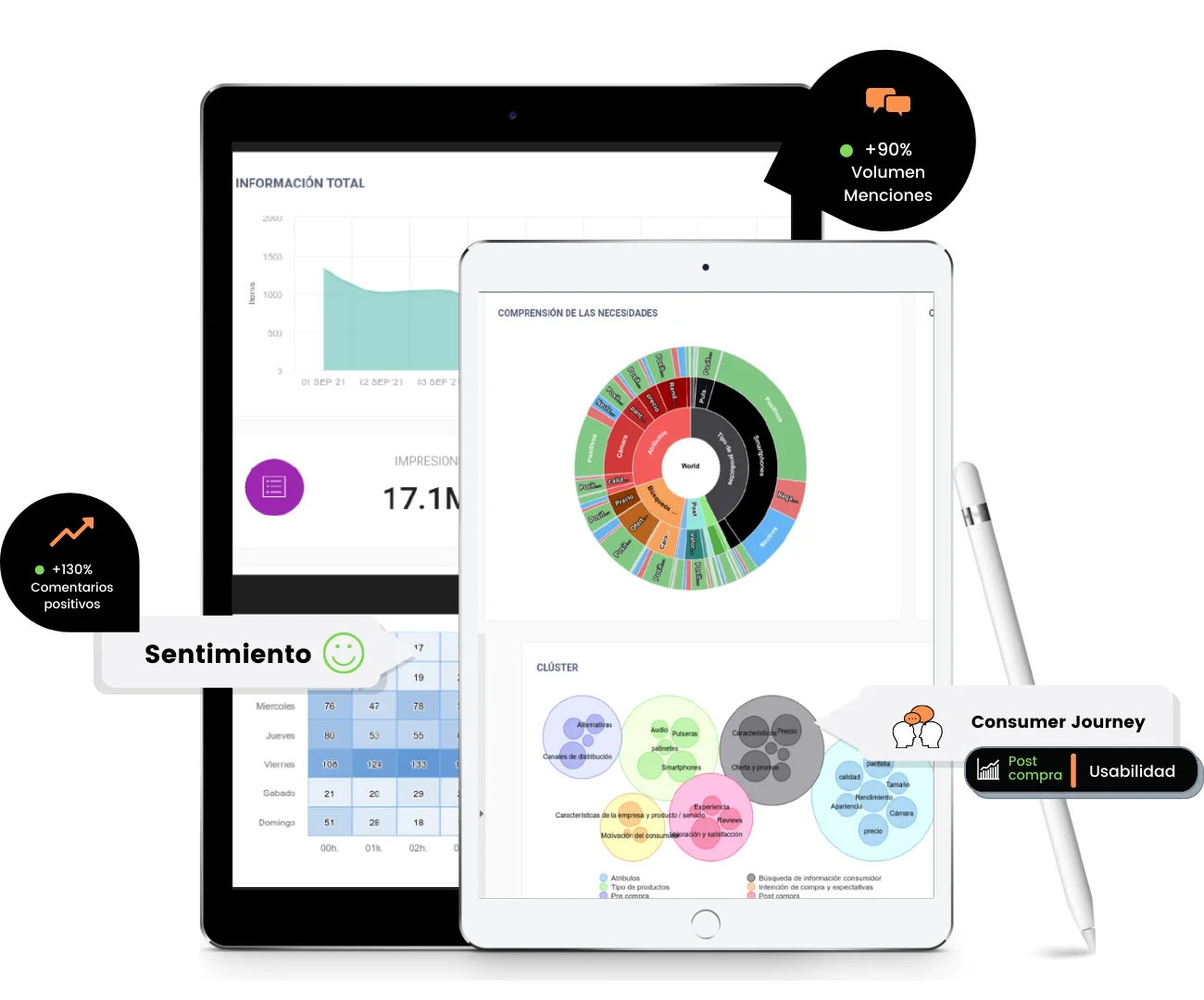
We use social listening to analyze social media, blogs, websites and forums
Identify, anticipate and react effectively to customer trends
Monitor your profiles or those of your competition and improve your social media strategy
Create custom social media reports in quickly and easily way
Detects your brand or your logo in images and digital media and discover its impact
Sector-specific solutions
We show you Atribus with a custom DEMO.
industry recognition
Leader 2022
G2 Crowd

Leader 2022
G2 Crowd

